he term "2FA" - short for "two-factor authentication" - has experienced something that I initially called "the Kleenex effect". After a bit of searching, I found out that "the Kleenex effect" is a real thing and even has a name: "genericide". Wikipedia defines it like this (lightly edited for clarity):
A trademark or brand name that, due to its popularity or significance, has become the generic name for a general class of product or service
Kleenex is a specific brand of facial tissue, but if we ask someone, "Hey, do you have any Kleenex?" we may be given a totally different brand of disposable handkerchief and not think twice about it; we use "Kleenex" and "facial tissue" interchangeably. Plenty of other brands have experienced genericide as well: Thermos, ChapStick, Aspirin, Dumpster, Band-Aid, Velcro, Hoover, Jet Ski, Speedo, and probably many more.
Though it is not a trademark or brand-name, "two-factor authentication" has experienced a similar thing. Here are some examples of what you might think of when you hear "2FA":
A text-message with a code:
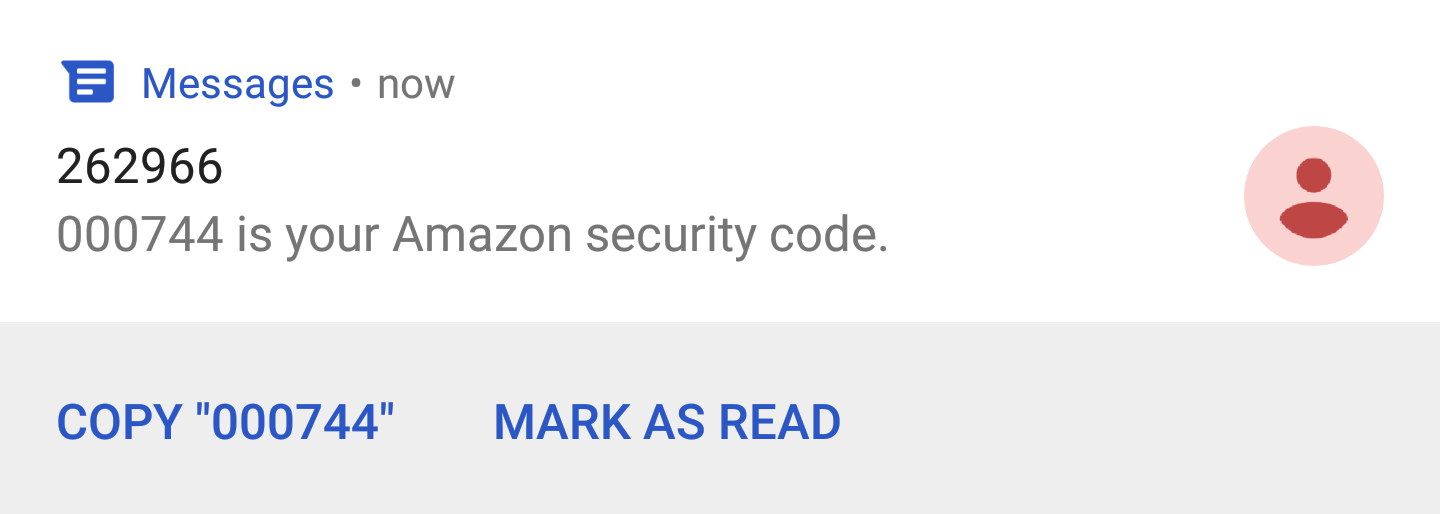
An email with the same sort of code:
A six-digit number that was generated by an app on your phone:
A small hardware token that you have to plug in to (or tap on) your computer or phone:

Here's the reality:
- Two of these are definitely not 2FA - the text-message code and email code
- One could be 2FA depending on how you do things - the number generated on your phone
- One is 2FA - the small hardware token
What we refer to as 2FA often only qualifies as two-step authentication, but two-factor authentication has become the general term, referring to any sort of process where you need to use something else in addition to your username and password to log in. I suppose you could call this phenomenon "technical genericide".
Normally this kind of thing wouldn't bother me much - these methods of "2FA" seem relatively similar, and using any of them makes you more secure, right?
This is where I start to have a problem. Yes, using even the weakest kind of two-step authentication will secure your accounts better than just a username and password but the difference between good 2FA and two-step authentication is quite large. To try and put it more succinctly: using the terms "two-step authentication" and "two-factor authentication" interchangeably might give people a false sense of security.
I would like to try and clear some of this up. Let's start by talking about "authentication" and "authentication factors":
What do "authentication" and "authentication factor" mean?
Imagine that your name is "Robert Paulson" and that you want to log into your online account at formerbodybuilders.com. You sit down with your laptop, open up your browser, and go to the formerbodybuilders.com login page where you are asked to provide your username and password.
"Authentication" means proving that you really are who you are claiming to be. In this example, authentication means proving to formerbodybuilders.com that you really are Robert Paulson.
An "authentication factor" is something that you use as proof during authentication. In this example, your password serves as the authentication factor; in theory, only Robert Paulson would know Robert Paulson's password.
Authentication Factors and 2FA
There are other authentication factors than just passwords. In general, there are three "types":
- Something you know: Passwords, PINs, answers to to "secret questions", etc.
- Something you have: This is something that you physically possess. Most commonly it is "something" that generates a short-lived six-digit number which you can only get from that "something". Google Authenticator and similar apps on your phone are in this category and may qualify as "true" 2FA depending on your configuration - in this case, your phone is the "something" you have. Smart cards and Yubikeys are also examples of something you have.
- Something you are: This generally refers to biometrics - fingerprints, retinal scans, and anything else that relies on what you "are". Your fingerprint is unique to you, so providing the correct fingerprint should (in theory) prove that you really are you.
Two-factor authentication means that you use two different "types" of authentication factors - for example, a password AND the six-digit number from your Google Authenticator app.
A related term is multi-factor authentication (MFA), which is the general term for using more than one type of authentication factor.
How strong is your "2FA"?
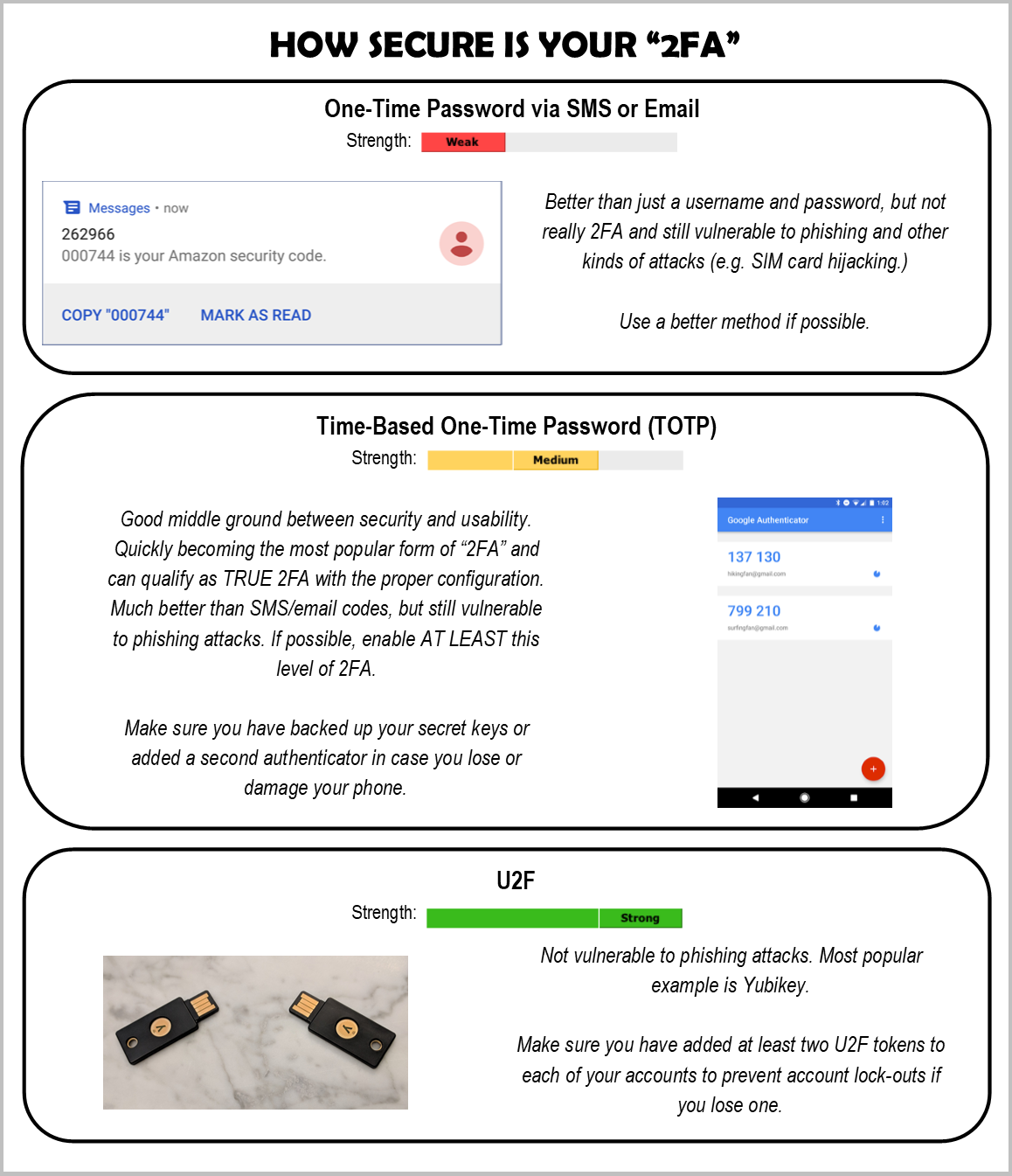
As I mentioned earlier, there is a huge difference between good two-factor and two-step authentication. Here is a comparison of the common forms of "2FA":
Temporary, one-time codes sent via SMS (text-message):
These do not give you two-factor authentication, only two-step. Typically people argue that your phone is the second factor (something you have), but text-messages are sent to a phone number, not the phone itself. There have been plenty of incidents where individuals have had their phone number hijacked and all incoming text-messages sent to an attackers phone, without any notification whatsoever (this is especially bad if you are also able to reset passwords via text-message). SMS codes are also valid for a relatively long time - generally at least 30 minutes - which undermines the "temporary" bit. Additionally, this does nothing to stop phishing attacks - what is stopping a malicious website from asking for your "portal code" as well as your username and password?
A quick side-note: security professionals will, with good reason, trash-talk SMS-based "2FA" because of how easily it is defeated - but if this is the only option that you are given, it is still absolutely better than just a username and password.
Temporary, one-time codes sent via email:
These suffer from the same issues that SMS codes do. You can retrieve the code from any device that can access your email, it can be phished, and the codes generally last even longer than the SMS codes do. I consider this method to be worse than SMS codes, which is why I listed it separately.
One-time passwords (OTP) generated by an authenticator app or physical device (hardware token):
These are generated with a technology called TOTP (time-based one-time password) and can fit the true definition of 2FA if you set up and use them appropriately. Typically this involves installing an app on your phone (Google Authenticator, Authy, Duo, etc) and then either copying the "secret key" or scanning a QR code like this:
This is quickly becoming a popular form of 2FA for its balance of security and usability, and is MUCH more preferable than the SMS or email codes - the TOTP number is ONLY available on the phone(s) or device(s) where you have configured TOTP for you account, so it is not vulnerable to the same issues that SMS and email codes are. At SEM, we are working on securing access to our external accounts with at least this level of 2FA.
There are some downsides, though. If you do not take proper precautions - like backing up your "secret key" and/or adding a second authenticator - you can end up locking yourself out of your accounts when your phone or hardware token is damaged or lost. TOTP is also vulnerable to phishing attacks. The codes are usually valid for only 30 seconds, the attackers just change their methods a bit.
A hardware token using U2F:
U2F stands for "Universal Second Factor" and is what I am most excited about in the future. You may be familiar with one of the most popular U2F devices: a Yubikey. I recently bought a couple of these myself:

Instead of typing in a code generated by a device, the second factor is built in to and provided by the device itself. Generally you use a U2F token by plugging the device into a USB port or tapping the device on something with NFC capabilities (like your phone).
This is immune from any phishing attacks - unless the attacker managers to trick you into giving them your physical U2F token, but I don't know if that is a problem that technology could solve anyway.
Because of the increased security, U2F also makes for better single-factor authentication and some have wondered if U2F may help replace passwords entirely.
The downsides here are that to avoid being locked out of your accounts (if you lose or destroy your U2F token) you need to buy at least two tokens, enable both for your account(s), and then ideally you would keep one of the tokens in a separate physical location. Besides the initial setup being a little more involved, this is not free - the Yubikeys I bought were $45 a piece.
U2F has not been adopted as widely as TOTP, but it is making progress. Check out Troy Hunt's post on enabling U2F for his Google account if you want a detailed real-life example of how this works.
In Summary:
I sort of went wide and shallow with the content here, and did end up skipping over a few things (like biometrics and push notifications). Feel free to drop a comment here or contact me if you have any questions!