EDIT 2020-08-03: It looks like the Bitcoin scam was conducted by three younger people (one is a minor) after a long period of reconnaissance and successful social engineering attacks against internal Twitter employees.
Sources:
- https://arstechnica.com/tech-policy/2020/07/florida-teen-arrested-charged-with-being-mastermind-of-twitter-hack/
- https://krebsonsecurity.com/2020/07/three-charged-in-july-15-twitter-compromise/
Honestly, in terms of criminality, I think they wasted a really good opportunity. They could've leveraged this access in all kinds of ways, but they chose to do a Bitcoin scam using a bunch of high-profile accounts. Not only is that kind of lame but it's also a really effective way to get caught. Nonetheless, a few people with pretty juvenile intentions managed to break into Twitter and that is pretty significant.
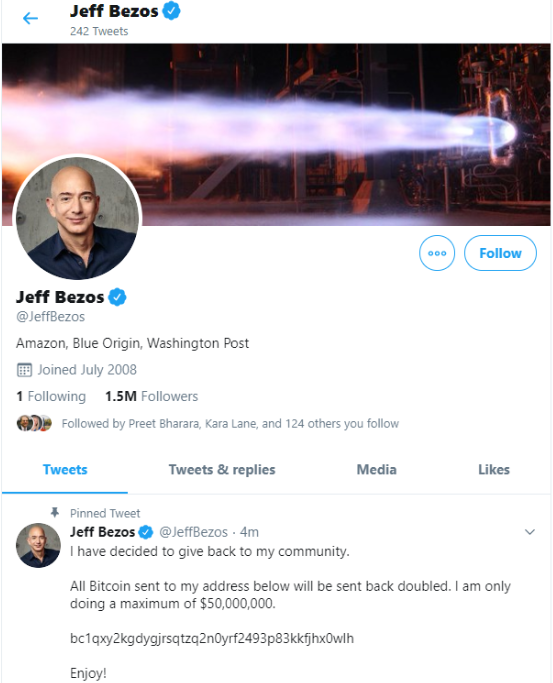
Last Wednesday, a bunch of high-profile accounts on Twitter were compromised and subsequently tweeted out cryptocurrency scams. Affected Twitter accounts included Apple, Uber, Jeff Bezos, Elon Musk, Barack Obama, Joe Biden, Warren Buffet, and Michael Bloomberg. The tweets looked something like this:
This is not the first time that a high-profile Twitter account has been compromised. For example, last August the account of Twitter's own CEO was compromised.
I've been following news about the mass-takeover of Twitter accounts since it occurred last Wednesday, and it seems that there are three possibilities for how these accounts were compromised:
- One or more Twitter employees were paid off to give hackers access to internal Twitter administrative tools. This allowed the hackers to gain access to the aforementioned high-profile accounts.
- Same as above, except that the Twitter employee(s) were victims of successful phishing attacks rather than being bribed.
- The Twitter accounts were compromised via SIM-swapping attacks.
Insider threat?
Possibility #1 is an example of an insider threat. In other words: someone who actually works for the company was knowingly involved in the account takeovers. I'm skeptical that this is what happened in the mass-compromise of accounts last Wednesday.
Bitcoin transactions are recorded on a public ledger called a "blockchain". A company called Elliptic ran some numbers and it appears that $120,000 was sent to the Bitcoin address in the scammy tweets. In my opinion, the ability to pay off one or more internal Twitter employees should be worth more than $120,000. I wouldn't be surprised if just the bribe itself cost that much money.
I suppose it could be a smokescreen of sorts to draw attention away from some other more subtle activity (think about what information you could gather from POTUS' DMs, for example), but I still don't find this very convincing - if you were careful about gathering information, you wouldn't need a smokescreen in the first place.
That being said, according to this article on Vice the (supposed) hackers say that they were able to bribe an internal employee.
Phishing attack?
Possibility #2 involves internal employees falling victim to a phishing attack. I think this is the most likely scenario, and it is the official conclusion from Twitter too.
The Twitter blog post notes that the phishing attack(s) were able to bypass their internal 2FA protections. This is significant. I've written before about how 2FA is a really good thing but is NOT a silver bullet, and this is a perfect example of that. It is imperative that employees receive regular phishing training in addition to enabling any and all technical protections. I still believe that the weakest link in any security program is going to be a human being.
This is also another reason that I believe in FIDO2/WebAuthN. This is a technology that makes it almost impossible to phish credentials, and also theoretically do passwordless logins in a secure way. Unfortunately it still has a ways to go in terms of adoption especially if you're a small business (or have an iPhone, but that's a discussion for another day). It is something that Twitter should have been able to implement for their internal tools, though.
If you're curious about what FIDO2 and WebAuthN are and can understand some more technical language, you might start here or here.
SIM-swapping attack?
A SIM-swapping attack is when a hacker is able to port your cell phone number to different SIM card, which they control. Usually hackers accomplish this by calling the victim's cell phone provider and convincing the provider that they are the victim (social engineering), and then asking the cell phone provider to transfer the phone number.
If you have your "2FA" configured to send the temporary code to your cell phone number, you can see why this would be a problem. I put 2FA in quotation marks because SMS-based codes are not really 2FA and are definitely not as secure (more on that here). This is what allowed Jack Dorsey's (Twitter's CEO) account to become compromised last August.
Previously, Twitter required you to initially set up 2FA with your cell phone number even if you wanted to use something else (like an authenticator app or Yubikey) and you could not disable the SMS version of "2FA". This meant that every single Twitter user with 2FA was vulnerable to SIM-swapping attacks. After their CEO's account was hacked using this exact method, they fixed the problem.
I don't think SIM-swapping was involved in the Twitter account takeovers from last Wednesday, but Brian Krebs has a good writeup on how criminals known for SIM-swapping attacks may be tied to incident.
Conclusion
- Make sure you (and your employees if applicable) are regularly training against phishing attacks.
- Use 2FA
- Use real 2FA if at all possible (i.e. not a code texted to your cell phone).
- Get excited about FIDO2 and WebAuthN